Tor and VPN
Should I use a VPN with Tor Browser?
Yes! Using Tor and a VPN together provides maximum security.
Should I use a VPN to connect to Tor, or use Tor to connect to a VPN?
Connect to a VPN first, then Tor. Read on to find out why.
Connect with a VPN, then Tor (Onion over VPN)
Connecting to a VPN first, then Tor (also known as “Tor over VPN” or “Onion over VPN”) gets you all the privacy protection of the Tor network, plus added protection that prevents any Tor node from seeing your home IP address. You will also not have to worry about being flagged by your home network for using Tor, as all that network will see is encrypted traffic to your VPN server.
Tor over VPN also provides access to the Tor network even where it is blocked, such as corporate and school networks, or certain countries.
Another advantage of Tor over VPN is that your VPN service will not see what you are doing inside the Tor network. And if there is a bug in the Tor Browser (as has happened before), connecting to VPN first will put an additional layer of security between that bug and you.
Setting it up is easy: Just connect to your favorite VPN server and then launch the Tor Browser.
Tor vs. VPN
The Tor network and VPNs are both privacy tools, but they work differently.
What is Tor?
Tor is an open network that anybody can join and contribute to, as well as use for free. Routing your data through the network anonymizes that data, but this process is slow and inefficient. The network does not collect any user information, although a malicious Tor node may keep limited logs. You do not need to trust the network, although you should assume that parts of it may be under surveillance.
What is a VPN?
In contrast, a VPN client routes all data through its network, even data being sent peer-to-peer (as with file sharing). It encrypts the data to prevent it from being seen by third parties, but, because it all passes through the VPN’s servers, a user must be able to trust that the VPN itself does not maintain any logs. At a minimum, a VPN will need to collect some user information, such as payment details.
Why not Tor first, then VPN?
Creating a tunnel through the Tor network and connecting from there to your VPN service (also known as “VPN over Tor”) is more difficult to set up.
ExpressVPN does not support this method as it does not increase your anonymity. While this setup does make it impossible for the exit node to see your traffic, it is now the VPN service that is able to see your traffic again.
In theory, a VPN that doesn’t keep activity or connection logs can be trusted with this information, but it reintroduces an element of trust into an otherwise trustless setup, leaving you with no anonymity advantages, only the slow speeds of the Tor network.
How does Tor work without a VPN?
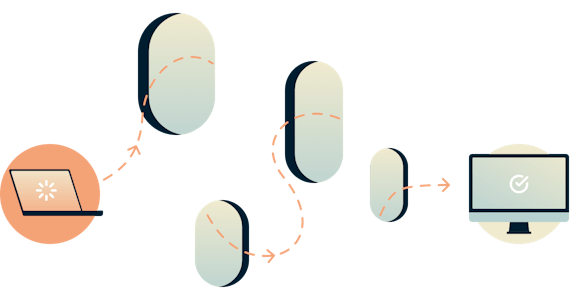
Tor functions like a layered series of proxy servers that route your traffic in a zig-zag around the internet before it reaches your destination (the layers give rise to the name, which stands for The Onion Router).
There are at least three hops your data travels through.
The entry node, which inevitably knows your IP address
The middle (or relay) node, which prevents the exit node from finding out which entry node you used and makes it very hard to correlate this information
The exit node, which knows what site you are connecting to, but does not know who you are
The three nodes separate your IP address from your destination and enable two individuals to communicate without either party, or any middleman, knowing who the other is.
The Tor network is typically accessed through the Tor Browser, which is derived from Firefox. The Tor Browser is optimized for security and privacy, unlike most other web browsers, which are optimized for speed and do not defend adequately against attacks such as browser fingerprinting.
Though Tor is pretty much the gold standard for anonymizing your internet traffic, the system is slow and inefficient. The Tor Browser by default only protects your browsing data, not other applications running on the side, which all have to be configured separately. A more secure option is TAILS, an entire operating system that allows you to route all your data, from all programs, through the Tor network.
Is it illegal to use the Tor Browser?
It is completely legal to use Tor. It is an important tool for dissidents and whistleblowers to communicate covertly. And some people use it to access websites censored in their country, including popular ones like Facebook. However, because a lot of illegal activity does take place over Tor, simply connecting to it could arouse suspicions from law enforcement or your ISP.
VPN + Tor = Best for security
Tor is an incredible privacy tool. When it comes to achieving anonymity on the internet, it is currently unbeatable, and it may be the only thing that can thwart the surveillance of a well-funded and sophisticated adversary.
Using Tor over VPN only increases your privacy. Connect to your VPN, then open the Tor Browser to gain access to the Tor network without your ISP being able to identify you as a Tor user.
Don’t have a VPN to use with Tor?
Try ExpressVPN risk-free.
If you’re not satisfied with ExpressVPN for whatever reason, you can get a full refund within 30 days of your order.