“Creative Commons Grand Cafe Van Gogh” by Thomas Leuthard, used under CC BY / Danger sign overlaid over photo.
Quick summary
What happened:
Apple just released an update for iOS that fixes a major security problem: it gave hackers a way to see exactly what you’re doing online, even if your browser is using https. This bug gave the bad guys a way to break the iOS devices’ attempts at encryption, and then see or modify what your iOS device is sending over the network, even when your browser tells you that it’s secure such as when logging into your online bank. (Here’s a technical explanation). What’s worse, this bug also impacts computers running OS X Mavericks, but as of the time of publication, Apple has yet to release a patch for this.
What to do now:
On your iOS device, go to System Settings and upgrade to the latest version of the iOS software. If you’re using OS X Mavericks on a computer, you’ll have to wait till Apple releases a patch and use extra security measures in the meantime.
Lessons learned:
Use a VPN. ExpressVPN protects any iOS device or OS X machine with this vulnerability. That’s because it adds an extra layer of encryption and anonymizes your traffic, making it a lot more difficult for the bad guys to attack the weakness.
The full story
On Friday, February 21st, Apple released an emergency SSL security update for iOS (7.0.6) to fix a bug in Apple’s official SSL/TLS library which skips over a crucial signature verification that encrypts communications. While the recently released patch is great for iOS users, OS X Mavericks remain vulnerable. Apple has yet to announce when we can expect a public fix. If the bug is unaddressed, Apple users are vulnerable to malicious man-in-the-middle attacks. If you’re on an open Wi-Fi network, a hacker could disguise him- or herself as coming from a trusted remote server, such as Gmail, Facebook, your online banking, or whatever—and intercept the encrypted traffic between your computer and the destination server. They can see personal information like your credit card number, address, phone number, personal correspondences, and more. Not only can they see the communication between your computer and the server, but they can modify its contents for more malicious purposes, too! Yikes! You can see if you’re affected by going to gotofail.com in Safari on your iPhone/iPad or on your computer.
How to protect yourself from the Apple SSL goto fail bug now
1. Update your operating system software now. Preferably on a secure network.
If you’re reading this and you haven’t run a software update on your iPhone/iPad/iOS device since Friday Feb 21st, then DO IT NOW! Go to Settings > General > Software Update. Unfortunately OS X Mavericks users will have to wait until the next patch is released. Security best practice: You should also be in the habit of keeping your operating system up to date, as developers habitually release security patches.
2. Use Chrome or Firefox for now.
Chrome and Firefox use their own SSL/TLS libraries and are reportedly fine for now.
Avoid using apps that native to the Apple operating system, like Mail, Safari, Calendar, etc. (A more complete list of vulnerable apps is available here.)
3. ALWAYS use a VPN on public Wi-Fi networks.
A VPN provides an additional layer of security for your connection on public Wi-Fi networks, like your favorite coffee shop, library, park, airport lounge…
Why you should have been using a VPN on public Wi-Fi… yesterday!
NEWSFLASH: The real issue here is that eavesdropping and snooping on public Wi-Fi has been a security threat long before the Apple SSL bug. In all the discussions about the goto fail bug, this is the real elephant in the room!
Most public Wi-Fi networks don’t encrypt data that’s transmitted through their networks, meaning that your personal information is in plain view (especially POP3, IMAP, and FTP info, which is transferred in plain text). Furthermore, software for eavesdropping is readily available to download and startlingly easy to use, and has been for a while. (Remember Firesheep?)
So don’t kid yourself. Even if Apple delivers a patch to fix the SSL bug, public Wi-Fi hotspots will continue to be unsecured, and hackers will continue to figure out ways to eavesdrop on your data. WE BELIEVE FIRMLY that any time you’re connecting to an unsecured or public Wi-Fi hotspot on any kind of device or operating system, you should be using a VPN. Don’t take a chance. Express VPN works by creating a secure tunnel between your computer and every website or application online, using high-strength 256-bit encryption to anonymize your data and make it indecipherable to hackers, spies, snoops, and all sorts of bad guys. 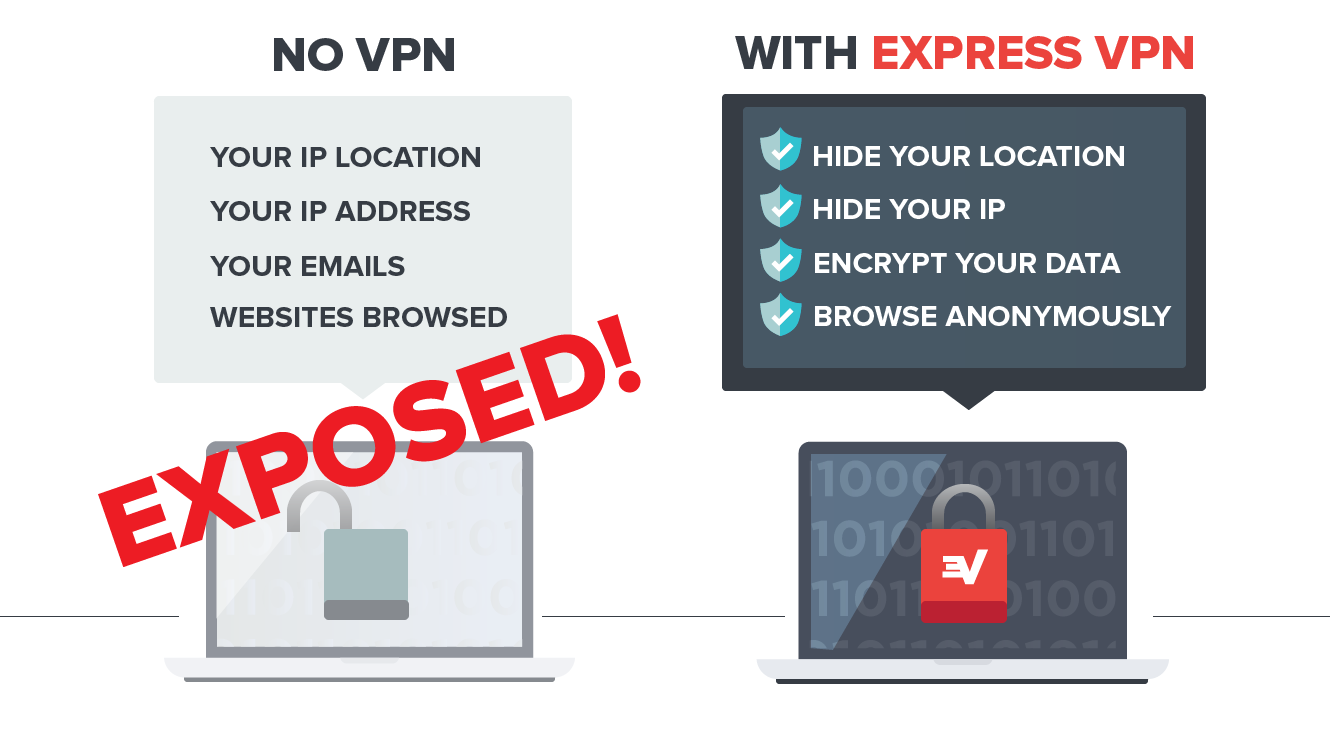 If you’re not already using a VPN whenever you’re on public Wi-Fi, it’s time you seriously considered it! Click here to get ExpressVPN and secure your Internet today.
If you’re not already using a VPN whenever you’re on public Wi-Fi, it’s time you seriously considered it! Click here to get ExpressVPN and secure your Internet today.




























Comments
Well thanks Jessica. Remote serving has certainly increased the possibilities of hacking especially over the public connections and thus validates the use of VPN on public Wi-Fi connections for better protection against alarming security threats.