Despite their shortcomings, passwords are still the de facto standard for authentication on the web.
ExpressVPN has already written about the benefits of creating secure passwords using Diceware, using password managers, and building another layer of security around your accounts with two-factor authentication.
But what happens behind the scenes? What measures can, and should, a website operator take to secure your passwords?
The birth of computer hacking
The first computer system that used passwords was the Compatible Time-Sharing System at the Massachusetts Institute of Technology, built in 1960. Time-sharing allowed the computer to be partitioned and used as several workstations.
Still, there were more researchers than workstations, and users were allocated limited time on the system (which some exhausted pretty quickly). To make sure the researchers stayed within their limits, each was assigned a unique password to log in with.
But, of course, with the first passwords came the first hacker. One researcher, Allan Scherr, made use of a system that allowed users to print out files via punch cards (computers had no screens in the 1960s). Scherr located and printed the file that stored the passwords, enabling him to log in as other users and use the computer for longer.
Today it’s considered grossly negligent to store passwords in clear text on a system, although the 2016 hack of the Russian social media site VK.com shows that some large sites still do. The VK.com passwords of 100 million users were stolen and are now up for sale.
Why hash functions are a one-way street
A hash function is a one-way encryption and acts much like a fingerprint. Every file, word, or text string is designated a hash “fingerprint,” which uniquely identifies the exact content of the original file.
Hashes can be used to determine information, but not what the data represents. One simple way to imagine how hashes work is with digit sums (the sum of all a number’s digits).
The digit sum of 9807347 is 9 + 8 + 0 + 7 + 3 + 4 + 7 = 38
Though it’s easy to see the digit sum of 987347 is 38, it’s impossible to calculate 987347 from the number 38.

SHA-256 offers a universe of permutations
Incredibly, 256 bits is a long enough output to uniquely identify every single atom in the observable universe (2^256 = 1.157920892×10⁷⁷).
Though, in theory, there could be two different values that both have the same SHA-256 hash. Such an event is called a hash collision, and the security of any hash function relies on them being undiscoverable.
The predecessor of SHA-2 (of which SHA-256 is a variant)—the once-popular SHA-1 algorithm—is known to be vulnerable to hash collisions. Though it’s worth noting, no one has ever found one.
Another once-popular hash, MD5, had so many vulnerabilities that it’s not a useful defense against malicious tampering of files.
Apart from encrypting passwords, hash functions can also be useful to ensure that files have not been tampered with, similar to cryptographic signatures, as an altered text string will alter the hash key.
Storing passwords as hashes, rather than clear text, makes it possible to check a password is correct without leaving the password vulnerable to hackers.
Salt and hash protects your passwords
If someone were able to hack a database that only contained hashed passwords, in theory, they would get no useful information. In reality, however, people reuse their passwords across many sites, or use common words in them, and there are many things a hacker can do to crack the hashes.
Every SHA-256 hash of the word ExpressVPN is always the same, on all systems. So if your username is Lexie and you use ExpressVPN as a password (don’t), a hacker could search for the hash “c9f45…3d185” among the passwords to see Lexie’s password is ExpressVPN.
Though this doesn’t sound particularly helpful on its own, there are lists of the top few thousand most-used passwords (which we know from previous hacks).
Using such a list, a hacker could search for the hashes of the common passwords and match them to usernames.
This type of attack is called a rainbow table, or dictionary, attack. There is not enough time left in the universe for an attacker to try every possible hash/password combination in a brute force attack. But there is enough time to try the most popularly used passwords, which would probably compromise a significant portion of the database.
Salting protects passwords by assigning them unique numbers
To protect against dictionary attacks, a database administrator can use a method called “salting,” where each password is assigned a unique random number. An SHA-256 hash of the combination of salt and password is then calculated, stored, and checked.
Alternatively, the password could be hashed, combined with the salt number, and the result hashed again.
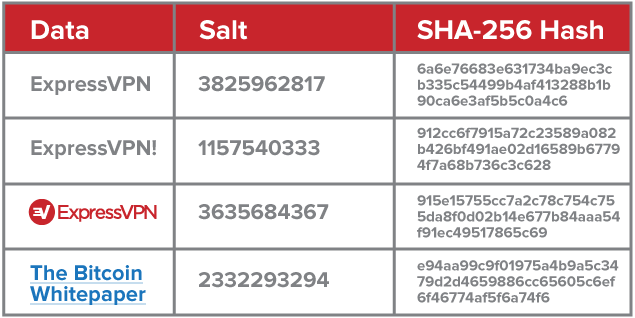
Due to the salting technique, creating a rainbow table is no longer attractive. The random numbers would make every hash unique, even if the user did not choose a unique password.
If a hacker wanted to target users with the password “Passw0rd!”, the salt number would keep the database safe.
The future of password systems
Passwords are far from optimal for online authentication. A good one is hard to remember, they are difficult to revoke, and once leaked might cause considerable damage.
Password managers can make passwords more user-friendly and help you create unique ones. They will also encourage you to change your login credentials regularly, which is necessary for good online security.
Perhaps in the future, we will move to alternative forms of authentication, such as public/private key pairs, possibly combined with hardware keys. In such a model you would only need to upload your public key once to a server when signing up, then never again.
While not necessarily magnitudes more secure than a properly implemented password solution, public/private key pairs are less likely to be applied incorrectly by both the user and the service.
What you can do to secure your passwords
Be aware that many of the services you are using today might have already lost control of your passwords. Maybe they don’t know about it yet, or maybe they’re refusing to publicly acknowledge it—protecting their image at the expense of the security of their users.
Use a random password generator and change your passwords into long random strings of letters and characters. You can also activate two-factor authentication on some services to add an extra layer of security.
It’s also a good idea to delete any accounts that you’re no longer using, in the hope that the service deletes your user data along with it.




























I have vpn from you guys.. flashed my router for it.. but a prob now…. i need portforwarding for my security camera’s.
can you please please create an update which makes it possible.
I hate all this eail stuff I don’t think ppl shld have to have to type in there email accounts every time.