“How to stay safe online!” is a common headline these days. We are told repeatedly that free public Wi-Fi is “dangerous,” that our private data is “vulnerable,” and that we should take steps to “protect” ourselves. These terms, however, are vague. As a result, the threat of “being hacked” can seem distant and irrelevant.
That’s why ExpressVPN set out to film a very real, specific attack that could happen to you today:
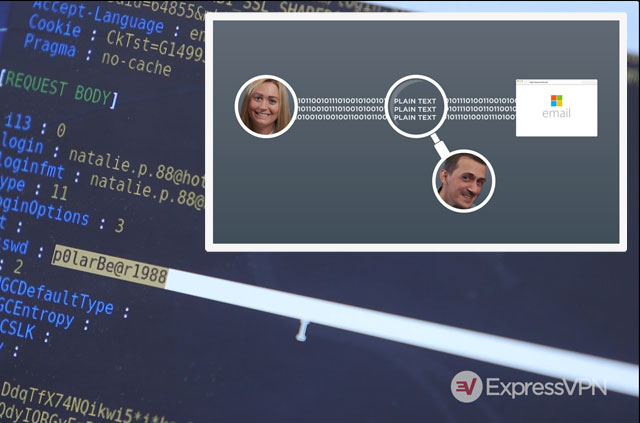
In the video above, Samet steals Natalie’s Hotmail password using a man-in-the-middle attack called SSL stripping. Scarier still, the same attack can work on sites like Amazon and Citibank.
What is SSL stripping?
In the video, Samet uses a $20 wireless adapter and a set of free penetration testing tools running on Kali Linux on a typical laptop to identify Natalie’s computer on the wireless network and listen to her traffic. That means he can see Natalie’s request to visit www.hotmail.com, intercept it, and forward it on to Hotmail from his own computer, pretending to be Natalie.
Hotmail wants Natalie to use HTTPS, so it sends back the login page encrypted using SSL, but because Samet is the man-in-the-middle, he can “strip” (i.e., remove) the SSL before forwarding it to Natalie. Natalie doesn’t know it, but when she types in her password and hits “Sign in,” she’s sending it in clear text straight to Samet. Samet adds back the SSL encryption before forwarding it on to Hotmail—and no one is the wiser.
If SSL stripping is so easy, why haven’t we heard about it before?
SSL stripping is quite well known among security professionals. It was first introduced at the 2009 Black Hat conference in Washington DC by Moxie Marlinspike, better known as the security genius behind the encrypted chat app Signal. Amazingly, the attack still works despite being more than 8 years old!
What did change is that some sites have implemented a new protocol called HSTS (HTTP Strict Transport Security) designed to thwart SSL stripping. Sites that use HSTS will only allow the browser to make requests in HTTPS, not plaintext HTTP like the kind that Samet first intercepted from Natalie.
SSL stripping no longer works with Facebook or Gmail because they have completely switched over to HTTPS and implemented HSTS. However, there are still many popular sites, like Hotmail, Amazon, eBay, and Citibank, that haven’t completely abandoned HTTP and thus aren’t yet eligible for HSTS.
How to protect against SSL stripping
SSL stripping might seem like a tough attack to defend against, because it works on many devices and networks. You are susceptible to SSL stripping whether you’re on mobile or desktop, Windows or Mac, and it doesn’t matter whether you’re on free public Wi-Fi or a password-protected private network. You could even get hacked by your next-door neighbor snooping on your home Wi-Fi! (Some enterprise networks, like those of corporations or schools, are configured to guard against attacks like SSL stripping.)
If you’re tech-savvy enough to recognize the HTTPS padlock icon missing from your browser’s address bar, you may just catch an SSL stripper in the act. But according to Samet, that kind of vigilance often isn’t enough:
“Just because the URL says ‘https’ and it looks legit, it doesn’t mean that you are secure and that someone on that network isn’t playing dirty. Which is why in my personal opinion it is highly recommended to use VPN.” —Samet
How a VPN prevents SSL stripping
In the second half of the video, Natalie connects to the secure ExpressVPN server in New York before logging into Hotmail. All her traffic is now sent through a private, encrypted tunnel instead of the public network Samet is listening on.
Now, none of Natalie’s traffic is visible to Samet, not even the initial request to Hotmail that he previously used to initiate the SSL strip. The attack running on Samet’s machine is stuck at a listening screen, waiting for traffic that will never come. At this point, a more malicious hacker would probably move on to another victim on the network who wasn’t using VPN!























Comments
Bad video. There wasn’t even an explanation given for how he identified her computer among all the visible ones.
Unrelatedly, are you saying that if an attacker is SSL-stripping your web traffic, you will know by simply checking if the padlock icon is missing/unlocked on your address bar?
Good advise, please !!! Goôd day.
Very useful Thanks.
Thanks for that comment.
Just a question.. If he is already a man in the middle and she then turns on the VPN won’t he see still see the traffic? If she’s already logged in to that person’s wife I he will still capture all the traffic even though its going through a VPN…Is this true?
Very useful info, thanks