The term “cryptocurrency,” a combination of “cryptography” and “currency,” alludes to the fact that cryptocurrencies are a form of digital money that uses cryptographic keys to identify its account holders and signatures to authenticate transactions. Cryptocurrencies only enter circulation through “mining,” a process that’s used both for creating new units of the currency and securing the ledger from tampering.
The mining process typically involves powerful, high-performance computers, which miners use to compete with one another to reap rewards. Before cryptocurrencies became as popular as they are today, it was possible to mine them with regular computers. Now, however, cryptocurrencies such as Bitcoin are typically mined in extensive farms that feature hundreds of computers working in unison and around the clock.

Photo: Wikimedia
With its immense growth in scale, cryptocurrency mining has become a very expensive affair, requiring steep amounts of capital for the initial infrastructure as well as high recurring monthly bills. This has led duplicitous hackers to seek workarounds in the form of cryptojacking.
What is cryptojacking?
Plainly speaking, cryptojacking is the illicit use of third-party devices such as laptops, tablets, or smartphones to secretly mine cryptocurrency without the knowledge or consent of device owners. This type of malicious hack steals a portion of your computer’s resources and dedicates it to solving cryptographic puzzles on behalf of the hacker.
As a victim of cryptojacking, you’ll be saddled with all the costs, such as high electricity bills and inefficient system performance, without reaping any of the rewards. Needless to say, it’s a situation that you would rather avoid.
Lots of cryptojacking software is designed to be subtle, so users don’t notice that something’s amiss. After all, it’s not like we’re in the habit of constantly checking system performance and examining the processes in our system tray. If our devices perform slower than usual, we blame the latest software update or point to the dozens of tabs open on our browser. And if our cooling fan turns on more often than it did before, we just assume that our device needs to be upgraded or serviced.
However, it’s likely these subtle signs that indicate the presence of cryptojacking software.
How do I detect cryptojacking?
If you feel that you have fallen victim to a cryptojacking scheme, the first thing you should do is check CPU usage.
For Mac users, simply navigate to Launchpad > Activity Monitor > CPU.
For Windows users, open up Task Manager > Processes > CPU.
A CPU running at normal levels should look something like this:
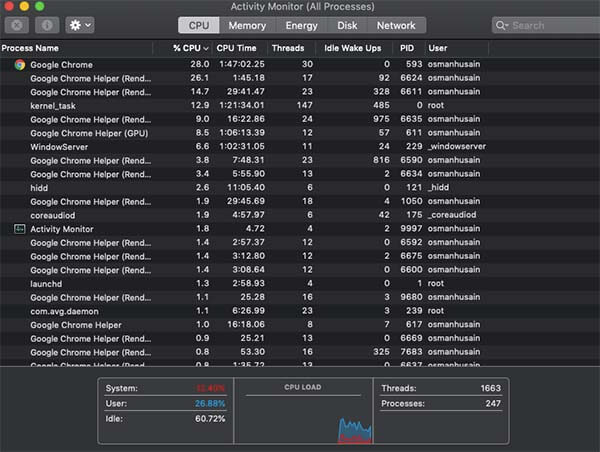
If your system utilization is at a high percentage, despite minimal use of processes and apps, it’s possible that you’ve fallen victim to a cryptojacking scheme.
Other telltale signs of cryptojacking are overheated CPUs and consistent laggy performance.
How can I guard against cryptojacking?
Malicious programs designed to covertly mine cryptocurrencies on your device spread just like any other virus or malware. Hence, to guard against them requires an adherence to prudent security practices.
For starters, this means refraining from clicking links in emails sent by people you don’t know or don’t trust. It’s also important to keep your devices updated at all times (we recommend turning on automatic updates) and only install software or apps from official marketplaces.
There are also some browser add-ons that claim to guard against cryptocurrency mining. For starters, the Opera browser has an in-built protection that guards against this threat, akin to ad-blockers on web pages.
If you prefer to stick with Chrome, you can download the No Coin extension, while Firefox users can utilize the NoMiner add-on.
We also recommend using a robust antivirus product, making sure to update it frequently and running a deep scan every few weeks. Ad blockers like uBlock Origin and Adblock Plus offer protection, too.
Is cryptojacking widespread?
The amount of cryptocurrency that can be mined from a single device is rather miniscule, but when cryptojacking software reaches hundreds of thousands of devices, it becomes very lucrative. Plus it entails zero cost for the hacker.
That’s precisely why cryptojacking is far more common than you might think. The Federal Trade Commission warns against it, urging users to be mindful of “scammers using your computer as their virtual ATM.” In 2017, Fortune declared cryptojacking the “next big cybersecurity threat.” Even Cristiano Ronaldo’s official website has fallen victim to cryptojacking, with dubious code capable of mining Monero surfacing a couple of years ago.
Cryptojacking isn’t likely to magically disappear anytime soon, and hackers may well come up with even more ingenious methods to extract our system resources for their benefit. However, as long as you remain cautious and alert, it’s certainly possible to avoid the deleterious effects.
On the flipside, if you want to share some of your excess computing resources to help a good cause, then check out Donate Your Tab.