How does VPN security work?
A VPN is an excellent tool for staying private online, but it also keeps you secure with encryption, tunneling, and some other advanced security features.
What is a secure VPN?
A VPN, or virtual private network, is a secure tunnel between your device and the internet. We call this a secure VPN connection because it’s encrypted and protected against external attacks.
Without a VPN, your unencrypted traffic is visible to others and may be vulnerable to manipulation, especially on unsecured public networks. That’s why using a VPN is an easy way to instantly improve your online security, no matter where you are.
How does a secure VPN work?
A VPN works by establishing a secure connection between a client (like your device) and a server (like the ones provided by ExpressVPN).
Your device connects to a remote access server (RAS) using valid credentials. These credentials are authenticated using any one of a number of methods called protocols. That’s the VPN’s first layer of security. Your device also uses client software to establish and maintain a safe VPN connection. The client software sets up a tunneled connection to the RAS, as well as managing the encryption that secures your connection. Let’s have a closer look at what these are.

Secure connections via tunneling
A VPN sends data privately over the internet through a secure process called tunneling. To understand tunneling, we have to remember that all data transmitted over the internet is split into small pieces called “packets.” Every packet also carries additional information, including the protocol (such as HTTP, Telnet, and so on) it’s being used for and the sender’s IP address.
On a VPN’s tunneled connection, every data packet is placed inside another data packet before it is sent over the internet. The process is called encapsulation.
It’s easy to imagine how useful encapsulation and tunneling are in securing your data. The outer packet provides a layer of security that keeps the contents safe from public view.
Secure data encryption
It’s not enough just to tunnel data sent over a VPN. The next layer of security is encryption, whereby data is encoded so that packets can only be read by your VPN client and server, which are securely connected together.
VPNs can use a number of security protocols to encrypt data. The most common are IPsec (internet protocol security) and OpenVPN. They work by:
Encrypting each encapsulated data packet’s contents with an encryption key. The key is shared only between the VPN’s server and clients.
Using a sub-protocol called Encapsulation Header to hide certain packet information, including the sender’s identity, during transmission.
These two key features, along with others, maintain your online privacy by protecting your data and identity.
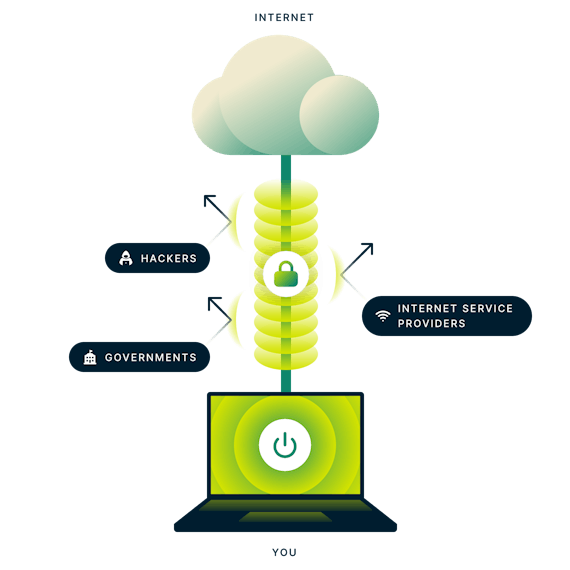
Why do you need a secure VPN?

To shield your browsing activity from third parties
ISPs have been known to share users’ browsing activity with data brokers and marketers who use it to serve targeted ads. By encrypting your traffic with a secure VPN, you can make your internet activity unreadable to your ISP and other third parties.
To protect against hacking
Using untrusted networks like public Wi-Fi hotspots can be dangerous. Using a secure VPN protects against man-in-the-middle attacks that allow hackers to intercept and manipulate your internet traffic.
To defeat censorship
Living or traveling in a country with internet censorship? Using a secure VPN allows you to break through firewalls to unblock websites and enjoy a free and open internet.
VPN security features
What are the most secure VPN protocols?
Lightway
Lightway is our most secure protocol, built from the ground up by the security experts at ExpressVPN. Lightway is open source and uses wolfSSL, a well-established cryptography library that is FIPS 140-2 validated—which means it has been rigorously vetted by third parties. Lightway’s core code has also been audited and open-sourced so that it can be transparently and widely scrutinized for security vulnerabilities.
OpenVPN
OpenVPN, a highly customizable VPN protocol that’s available for a wide variety of platforms, has also been extensively audited by multiple neutral experts. Its open-source implementations are available for anyone to inspect and improve.
IKEv2
IKEv2 is considered to be a lighter and more stable option than OpenVPN, particularly great for use on mobile devices across all platforms. It is also considered secure, though it is only available over UDP, which is blocked by some firewalls.
Download the best VPN for security
To use ExpressVPN, sign up below and download a secure VPN app for Windows, Mac, Android, iOS, Linux, routers, and many other devices. Choose a server location in one of 105 countries around the world to use the internet privately and securely.
Don’t see your device? You can also view manual configurations and setup tutorials for a wide range of other devices and platforms.
Set up a VPN for all your devices:
Frequently asked questions
Are VPNs really secure?
Yes, if you use a high-quality VPN. When using ExpressVPN, your data is transmitted through a tunnel secured with AES-256, the same encryption standard adopted by the U.S. government and used by security experts worldwide to protect classified information. It’s impenetrable by attackers and other third parties, keeping your online activity private.
Can a VPN be hacked?
Vulnerabilities can weaken a VPN, but ExpressVPN takes your privacy extremely seriously and takes full measures to ensure the security of our service. As a safeguard, ExpressVPN servers do not store users’ connection or traffic logs, plus our proprietary TrustedServer technology ensures all data is wiped from servers with every reboot.
Meanwhile, using a VPN protects you from hacking methods such as packet sniffing and man-in-the-middle attacks. In fact, using a VPN is good practice for every type of connection, but can be particularly useful when browsing unsecured HTTP websites. Expats, travelers, and all kinds of on-the-go individuals should use a VPN whenever they're on untrusted networks.
Do VPNs really protect you?
High-quality VPNs such as ExpressVPN protect your identity, data, and privacy in various ways. Your online traffic is shielded in an encrypted tunnel so no one can see your activity or sensitive information (such as during online banking). At the same time, a VPN gives you a different IP address that is shared with thousands of other VPN users—this raises your anonymity and makes it virtually impossible for anyone to trace your activity back to you.
Can VPN providers be trusted?
Security levels vary widely among VPN providers. That’s why ExpressVPN co-founded the VPN Trust Initiative, an industry group, which launched a set of principles to help consumers evaluate VPN services.
ExpressVPN’s Trust Center provides extensive additional information on our security practices.
How much does a VPN cost?
ExpressVPN offers subscriptions in 1-month, 6-month, and 12-month pricing plans. Visit the order page to find the plan that’s right for you.
Learn more about using a VPN

Encrypt your data
Strong encryption protects your data and communication

How fast is your VPN?
Find out what affects VPN speeds and how to find the fastest server for you
Security and privacy
Ready to try a secure VPN?
Stay safe online with ExpressVPN. You’re covered by our 30-day money-back guarantee.
